Corporate governance only applies to legal entities, but ISG applies to any ISMS organisation

Governance
Introduction
This article summarises the findings of IMS-Smart’s research conducted into information security and corporate governance conducted over the period 2016-2018. Some of these research findings were fed into the revision of ISO/IEC 27014 — Governance of information security, published in December 2020. Read the standard to see which of our findings were incorporated.
Whence does the concept of governance originate?
Interest in corporate governance has arisen around the world because of various scandals, where the investing public has been ‘ripped off’ by the unethical conduct of senior executives. Such scandals include: South Sea Bubble, Kruger, Salad Oil company, Equity Funding, Polly Peck, Maxwell Pensions, Enron, WorldCom, … and more recently the events that led to the collapse of the banking industry due to the sub-prime mortgage crisis. These scandals have caused the introduction of new laws and regulations, such as Turnbull, OECD, Sarbanes-Oxley, the EU directive on corporate governance, etc.
The principles that were established by the Organisation for Economic Co-operation and Development (OECD) in 2004 cover:
- the rights of shareholders and key ownership functions;
- the equitable treatment of shareholders;
- the role of stakeholders in corporate governance;
- disclosure and transparency; and
- the responsibilities of the Board.
These principles were updated in 2015. They point out that an important function of the board is to establish internal control systems covering the use of corporate assets and to guard against abusive related party transactions.
What is the relationship between corporate entities and ISMS organisations?
For sake of clarity, an organisation in an ISMS context can be a subset of a legal entity, a whole legal entity or a set of subsets of legal entities. In a corporate governance context, the organisation can only be a legal entity. Top management is therefore the Board of Directors (or equivalent). Moreover, the organisation’s objectives will be its business objectives.
What is the relationship between governance and internal control?
Internal control is how top management marshals its resources to achieve the organisation’s business objectives.
There are two parts:
- the part for doing the job;
- the part for doing the job the way the boss wants it done.
This rather elegant description of internal control was how the late William List, CA, FBCS, retired computer audit partner at KPMG, and a distinguished member of the UK shadow committee to JTC 1 SC 27 WG1Joint Technical Committee 1 Sub Committee 27 Working Group 1 chose to described it.
The first part concerns the exploitation of opportunities in the pursuance of the organisation’s business objectives. This is somewhat essential. Without it, there would be no way for the organisation to achieve its objectives, and consequently the Board would fail in its responsibilities.
The exploitation of opportunities gives rise to risk. This is where the second part of internal control comes into play. Thus, there is a link between opportunity exploitation and risk management.
Moreover, it should be evident from List’s description that if the boss is corrupt, the organisation’s system of internal control will corrupt the entire organisation. Thus, in accordance with the OECD principles, three elements are required:
- the exploitation of opportunities to achieve the organisation’s business objectives;
- the management of risk, attendant on the chosen course of opportunity exploitation; and
- the means to guard against abuse.
- societal responsibility.
You can read more about the relationship between internal control and the IMS-Smart philosophy here…
How can we do this in practice?
The following diagram presents an Information Security Governance framework. It presents a model based on five processes: REPORT, OVERSIGHT, DIRECTION, MONITORING and EVALUATION.
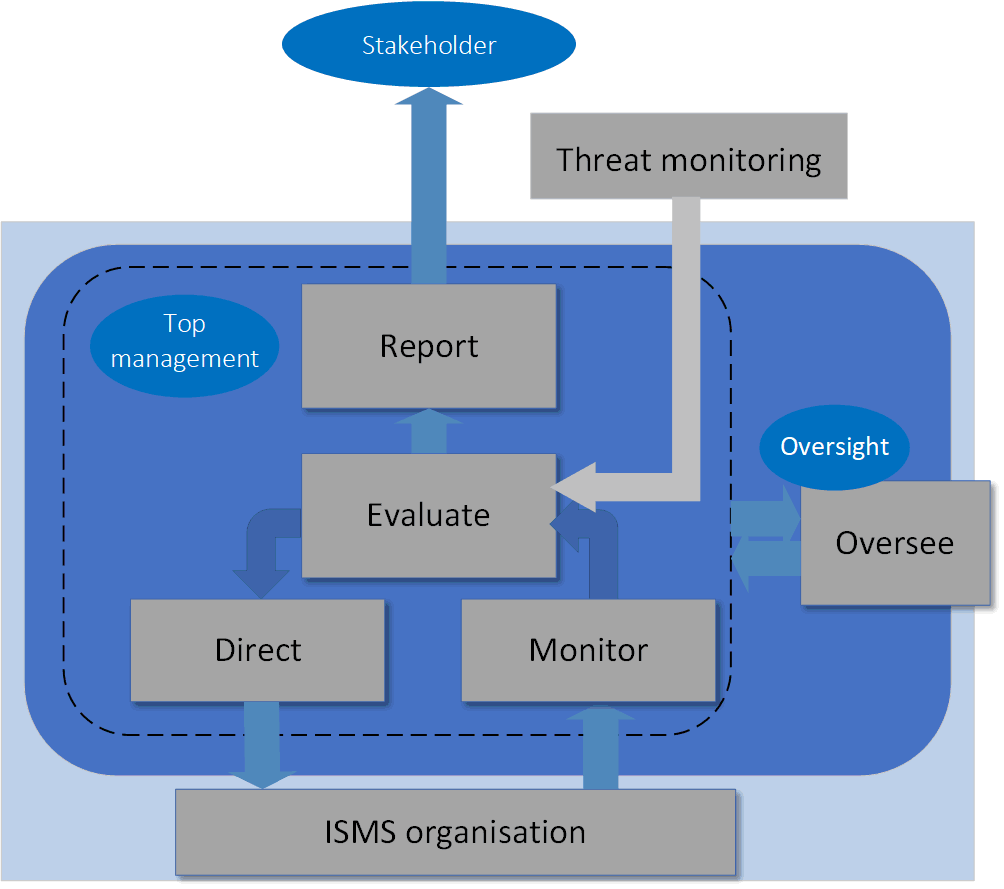
The effect of this framework is to give substance to the activities of the top management of the ISMS. According to all management system standards, and ISO/IEC 27001 is no exception, top management is responsible for setting the direction of the ISMS organisation, and this is shown in the framework diagram (DIRECT). However, the framework shows that top management is also responsible for:
- MONITORing the activities of the ISMS organisation;
- EVALUATing the performance of the ISMS organisation against its objectives
These activities should form part of the management review process, but there is an implication that this activity should be practised frequently.
The framework also shows that there is an OVERSIGHT activity, which in practice can be provided by an external body, for example a certification body.
Finally, the framework points out that there should be:
- a REPORTing mechanism, which could be the provision of reports to HQ (if the organisation is a subsidiary), to shareholders and to the public, (e.g., via news items published on the organisation’s website);
- an external monitoring function to assist it to evaluate the performance of the ISMS organisation against external benchmarks such as THREATs. This activity would be independent of any threat monitoring function performed within the ISMS organisation.
What is information security governance?
The general case
The first point to note is that the information security objectives of the organisation are not the same as its business objectives, and may not even be a subset of them: they are related to what the organisation has chosen to achieve in managing its information security risks.
Taking the sequence:
business objectives – opportunity exploitation – risks
some risks will be information security risks, and it is these risks that are within scope of the ISMS.
From an information security governance perspective, it is necessary for top management to ensure that:
- the information security objectives of the ISMS relate to the treatment of those information security risks that are attendant on its chosen course of opportunity exploitation;
- the ISMS manages those risks;
- the ISMS maintains the means to guard against abuse, consistent with the anti-abuse mechanisms it employs at the corporate level; and
- there are controls that ensure that the information and communications technology (ICT), or indeed any other entity within scope of the ISMS, is not used to compromise the information security of other organisations .
Note that the top management of the corporate entity and the top management of the ISMS organisation are one and the same thing. However, when referring to the ISMS, a top manager should only be considering information security, albeit such consideration should be clearly in the context of achieving the corporate business objectives.
Subsets of corporate entities
Top management
In the case where the ISMS organisation is a subset of the corporate entity, this description of information governance will still work, although, in this case, the top management of the ISMS organisation does not necessarily have the same membership as the top management of the corporate entity. Indeed, the two management teams might not have anyone in common. In such cases, top management of the ISMS organisation cannot work entirely independently of the top management of the corporate entity
A variety of cases
There are three cases:
CASE A: The ISMS organisation is responsible for managing its corporate entity’s information security risks; it does not own any corporate objectives.
CASE B: The ISMS organisation operates autonomously, in which case it has its own business objectives and does not contribute to the attainment of other corporate objectives, opportunity exploitation or risk management.
CASE C: The ISMS organisation has delegated responsibility for achieving certain corporate objectives, or pursuing certain courses of opportunity exploitation.
Case A
The ISMS organisation must regard the information security risks, attendant on the corporate entity’s chosen course of opportunity exploitation, as interested party requirements and act accordingly. The anti-abuse mechanism employed by the corporate entity should apply universally throughout the corporate entity. It will apply to the ISMS organisation.
Case B
In this case, the ISMS organisation behaves as if it is a corporate entity. The information security governance requirements for top management, given in 5.1 above, apply. The anti- abuse mechanism should be consistent with that employed in the associated corporate entity, if such exists. Otherwise it is created by the top management of the ISMS organisation consistent with its needs.
Case C
This is a combination of Case A and Case B. The exact balance between A and B being dependent upon the responsibilities given to the ISMS organisation by the corporate entity
Sets of subsets of legal entities
In the case where the ISMS organisation is a set of subsets of legal entities, there will exist a set of mutual business objectives that bind the collection of legal entities together. The cooperative entity will pursue a course of opportunity exploitation in attempt to fulfil those objectives. It is the information security risks attendant on such exploitation that are within scope of that ISMS. There should also be a mechanism within the cooperative entity to combat abuse, and that will apply to the ISMS.
Summary
Thus, it can be seen that, whilst corporate governance applies only to whole legal entities, the concept of information security governance can be applied to all types of ISMS organisation.
.jpg)

you consent to that site setting authentication session cookies
