| |
The IMS-Smart Assistant
David Brewer’s book: “ISO/IEC 27001:2022 — Mastering Risk Assessment and the Statement of Applicability”, advocates an innovative approach to performing the ISO/IEC 27001 risk management processes — risk assessment, risk treatment and the statement of applicability (SOA). It uses an 182 control set, much of it derived from the control purpose and guidance text in ISO/IEC 27002:2022, in addition to the control text which makes up ISO/IEC 27001, Annex A. Thus, it permits organisations to take advantage of the richness of ISO/IEC 27002 leading to a more comprehensive set of necessary controls, and thus better information security.
It consists of five easy steps:
- Answer questions regarding the characteristics of your organisation, your preferences, the impact of the loss of confidentiality, integrity and availability, and the likelihood that certain events will occur.
- Answer questions regarding the information security measures that you have in place (or intend to put in place).
- Review the risk stories and decide how effective they are about reducing your information security risks to an acceptable level.
- Answer some questions about your necessary information security controls (e.g. their implementation status) and excluded ISO/IEC 27001, Annex A controls.
- Export the results and incorporate them into your existing ISMS.
How is this possible?
- BS 7799-3:2017Information security management systems — Part 3: Guidelines for information security risk management (revision of BS ISO/IEC 27005:2011), Table 4, page 13
Please note:
ISO/IEC 27005:2022 (Guidance on managing information security risk) has just been published and incorporates much of BS 7799-3.
Please also note:
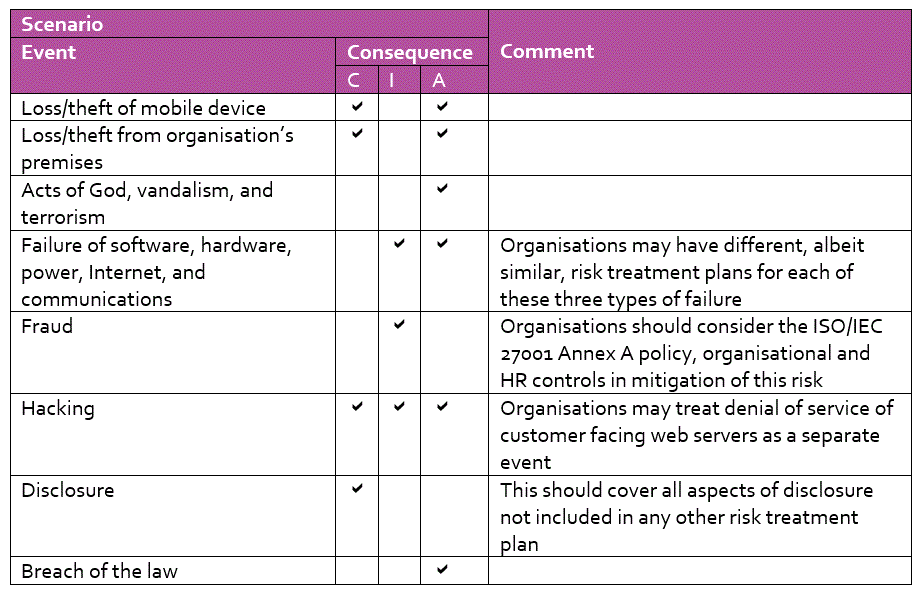
Whilst ISO/IEC 27001 does not use the term “risk register” (and therefore there is no requirement to have one), the definition of a risk register given in ISO Guide 73 is “record of information about identified risks”. Therefore, a record of the risks that you have identified and assessed in fulfilment of ISO/IEC 27001, Clause 6.1.2, constitutes a risk register. Specifically, the risks identified and assessed in the IMS-Smart On-Line constitutes a risk register. presented a set of risks in terms of example event-scenarios and consequences that give coverageThis is an essential property of the chosen event-scenarios. Expand the more detailed explanation accordion to find out why. of the controls in ISO/IEC 27001 Annex A. A fully ISO/IEC 27001 conformant risk assessment can therefore be performed just by estimating the likelihood of the occurrence of each of these events and the severity of their consequences.
- Once you have determined the controls necessary to mitigate these risks, coverageThis is an essential property of the chosen event-scenarios. Expand the more detailed explanation accordion to find out why. ensures that comparison with the reference controls in ISO/IEC 27001 Annex A is guaranteed not to discover any control that you have inadvertently overlooked.
This approach greatly speeds up the process of risk assessment, risk treatment and production of your statement of applicability.
Want a more detailed explanation?
Sufficiency of the chosen event scenarios
The purpose of the ISO/IEC 27001 risk assessment and risk treatment requirements is to determine your necessary controls. The SOA requirement is to compare your necessary controls so determined with those in the reference of controls in ISO/IEC 27001, Annex A.
Early research work by Brewer and Nash showed that Annex A controls can be mapped onto a few event scenarios. Thus, consideration of just those event scenarios (referred to as the “standard set”) guarantees that a comparison of the necessary controls I.e., those that the organisation has determined as being necessary to mitigate those risks with the Annex A controls will not detect any necessary control that has been inadvertently omitted (because each Annex A control is used in the event scenarios at least once).
Recent research has confirmed that the control set, which is the third editions of ISO/IEC 27001 and 2, best maps onto the nine event scenarios.
As pointed out in BS 7799-3:2017“Information security management systems — Part 3: Guidelines for information security risk management (revision of BS ISO/IEC 27005:2011)”, Clause 7.2.2, page 13, which states: “If a new scenario fails to identify any additional necessary controls, it is redundant.”, there is no need to consider additional scenarios as they will not determine any Annex A control that has not been considered already. Therefore, these event-scenarios are sufficient for the purposes of ISO/IEC 27001 risk assessment.
Sufficiency of the SOA processes
Performing the comparison
Typically, organisations consider each Annex A control in turn. If they do something like was it says, they mark it as applicable and declare it as such in their SOA. If they don’t do it (and assuming that this result doesn’t identify an overlooked necessary control), then they declare it in their SOA as being not applicable and justify the exclusion as required by ISO/IEC 27001. The structure of their SOA follows that of Annex A.
Unfortunately, if they do not do exactly what it says in Annex A for the controls they have marked as applicable, they can be given a nonconformity in a certification audit. This is because the requirement is to include the necessary controls in the SOA, not to identify applicable Annex A controls.
The safest approach is to use the variation device described in ISO/IEC 27007“Guidelines for information security management systems auditing”, Clause A.4, page 12: if one does something like what it says in Annex A, write down exactly what you do, declare it as a necessary control in the SOA and associate it with that Annex A control.
Moreover, it is also prudent to consult the guidance text in ISO/IEC 27002 as the control specifications in ISO/IEC 27001, Annex A are just summaries and sometimes fail to capture important control characteristics.
Reversing the process
The introduction to ISO/IEC 27001 states that requirements can be performed in any order. Why not then reverse the order of Clauses 6.1.3 b) and c), i.e., use the comparison process to determine the necessary controls?
For this to work:
- The standard event-scenarios are mapped to a set of questions, which in turn map to the reference controls (e.g. the Annex A controls). The mapping of Annex A controls to event-scenarios is preserved, thus preserving the guarantee of event scenario sufficiency for risk assessment.
- The questions are derived from the ISO/IEC 27002 control guidance as well as the ISO/IEC 27001, Annex A control descriptions and objectives.
- The permitted answers to these questions are:
- Yes: the statement form of the questionFor example: the statement form of the question “Does the organisation do X?” is “The organisation does X”. is used as the specification of the necessary control in the SOA;
- Similar: replace the question with a similar question to which the answer is “yes” and use the statement form of the replacement question as the specification of the necessary control in the SOA;
- No: if the question corresponds to an Annex A controlThe book and SAAS use a reference control set that is a superset of the current Annex A controls. If the answer to a question that relates to a new edition control, is “no” then there is no requirement to include the rationale in the SOA, ask why, and use the answer as the rationale for excluding that Annex A control in the SOA.
Generation of risk treatment plans
The risk treatment plans (RTP) are constructed using the statement forms of the questions used to generate the necessary controlsI.e., those answered “yes” and “similar”. In the case of “similar”, the statement form of the replacement question is used. in the SOA. The questions are mapped not only to the appropriate event scenario, but also to its position in the RTPI.e., prevent, detect. or react, and even the order of presentation so that the RTP reads well. Users of the SAAS can make adjustments to such text if they wish..
The risk assessment answers are used to generate the inherent risks. A similar set of questions and answers facilitate the determination of the residual risks. Risk treatment plan generation is thereby automatic.
Conclusion
The SOA is constructed from the answers to questions that map to all the controls in the reference set, which in turn are mapped to the event scenarios and their positions in the corresponding RTPs. Inherent and residual risks are determined by the answers to other questions pertinent to the event scenario and the necessary control text. Thus, all that is needed to perform the ISO/IEC 27001 risk assessment and risk treatment processes, and produce the SOA is the standard events specification, reference control set specifications, questions, and the instructions given in the book and automated in the SAAS.
The IMS-Smart SAAS that automated the prescription given in the book has now been withdrawn and replaced with an emulator that is part of IMS-Smart On-Line. It uses the same database, to if you decide to buy an IMS-Smart On-Line licence, there will be no need to exporting and importing of data.
The layout of the emulator is similar to that of IMS-Smart On-Line, with two differences: the welcome page is a dashboard (just like the original Assistant SAAS) and, of course, not all the pages in IMS-Smart On-Line are displayed or accessible.
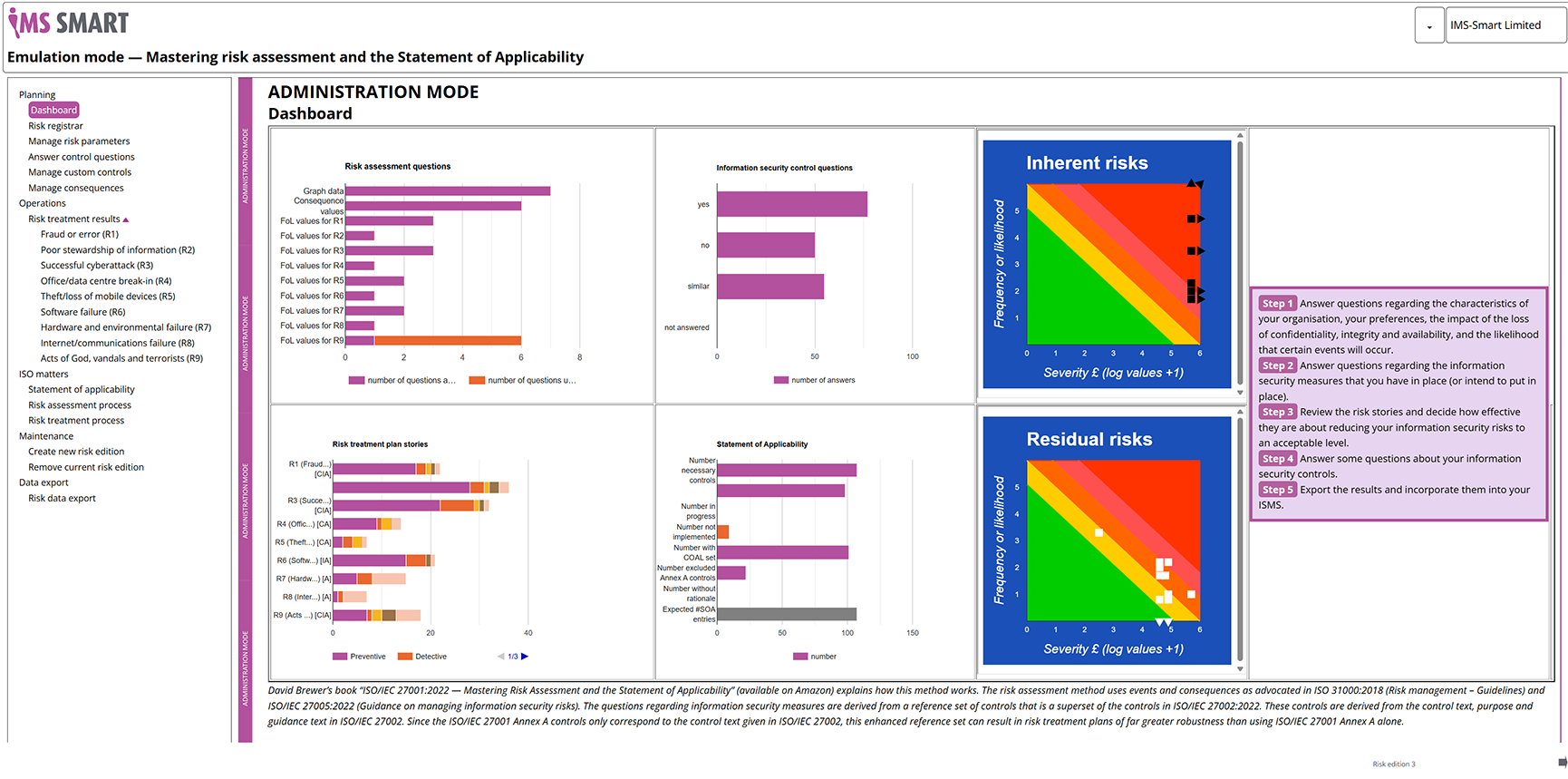
Dashboard
The home screen of the Assistant is a dashboard showing just where you are in terms of answering the various questions and other activities necessary to complete the ISO/IEC 27001 risk assessment, treatment and SOA processes.
Other pages
The layout and purpose of other assistant pages are identical to those in IMS-Smart On-Line. Indeed the pages share the same code.
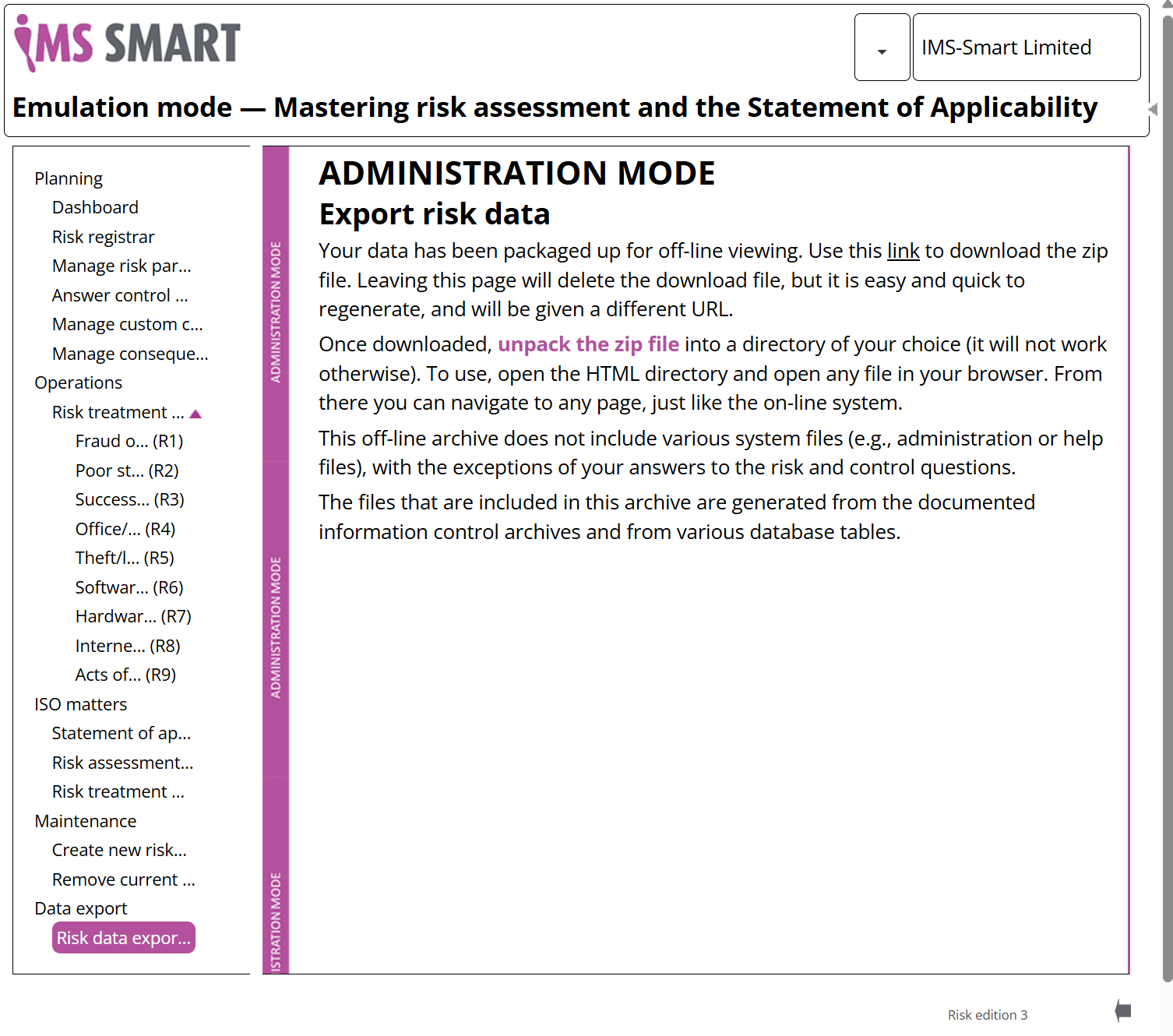
Exporting data
When the Assistant is first used, not all of its functions (pages) are available. The status of your instance of the Assistant is “in progress”. Risk data can only be exported when the status becomes “ready to export”. This happens when:
- The risk questions concerning the severity of consequence for the loss of confidentiality, integrity and availability have been answered
- All the control questions that correspond to ISO/IEC 27001 Annex A controls have been answered.
Pricing and purchase
The assistant is available free of charge for one year. The book “ISO/IEC 27001:2022 — Mastering Risk Assessment and the Statement of Applicability” (available to buy on Amazon) explains the method in detail and can be used without the Assistant. However, the Assistant renders the method described in the book far easier to use. Ideally, buy the book and use the Assistant.
|
|


.jpg)
