Full details are in “An introduction to ISO/IEC 27001:2022/Amd 1:2024” by David Brewer

ISO/IEC 27001 and other management system standards
- ISO/IEC 27001 — ISMS requirements (this page)
- ISO/IEC 27002 — Information security controls (the new edition)
- The Statement of Applicability (the bridge between ISO/IEC 27001 and ISO/IEC 27002)
- Risks and opportunities)
- ISO/IEC 27014 — Governance
- ISO/IEC 27004 — Monitoring, measurements, analysis, and evaluation
- ISO/IEC 27007 — Guidance for auditors
Introduction
All new and revised management system standards conform to the ISO Directives concerning high level structure and identical core text. The idea is that requirements that ought to be the same for all management system standards (e.g. corrective action) ought to be identically worded – and now they are. Requirements that are peculiar to a particular discipline (e.g. quality) are incorporated in what is known as “discipline-specific text”. Full details are in David Brewer’s book: “Understanding the new ISO management system standards”. The third edition of ISO/IEC 27001 was published in October 2022 and the first amendment in February 2024.
Structure
The following figure shows the high level structure (blue text) together with the discipline-specific requirement headings for ISO/IEC 27001:2022/Amd 1:2024.
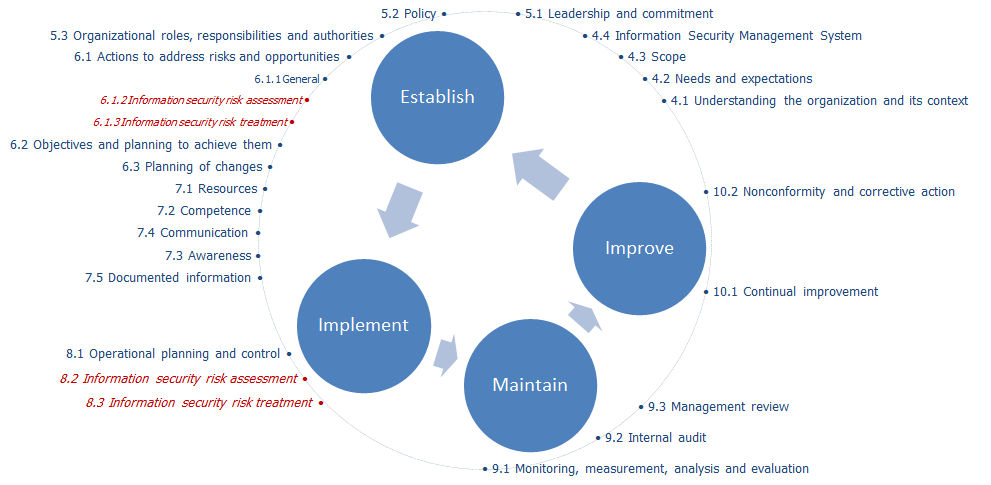
A detailed explanation of ISO/IEC 27001:2022/Amd 1:2024 is given in in David Brewer’s book: “An introduction to ISO/IEC 27001:2022/Amd 1:2024” 5th Edition”.
ISO/IEC 27001:2022/Amd 1:2024
ISO/IEC 27001 specifies the requirements for an Information Security Management System (ISMS). In summary:
- A management system is a way of life, a journey not a destination. To best adapt the standard to the context and established doctrine and culture of an organisation, the standard specifies what an organisation must must be done to achieve conformance not how it is to be done
 This is like being given the ingredients and told to make a cake, but not being given the recipe. You cannot buy an ISMS like a car or an off-the-peg suit of clothes. It is more like a custom car or bepoke tailoring, designed and crafted to fit the driver or wearer, or in the case of your ISMS, your organisation..
This is like being given the ingredients and told to make a cake, but not being given the recipe. You cannot buy an ISMS like a car or an off-the-peg suit of clothes. It is more like a custom car or bepoke tailoring, designed and crafted to fit the driver or wearer, or in the case of your ISMS, your organisation.. - The focus of ISO/IEC 27001 is on preserving the confidentiality, integrity, and availability of information within scope of the ISMS.
- The standard requires organisations to determine the information security controls that an organisation needs through the process of risk assessment and risk treatment.
- The risk assessment requirements are aligned with ISO 31000 (“Risk management — principles and guidelines”). The easiest way to do this is to consider events and consequences.
- As a safety net to ensure that no necessary control has been inadvertently overlooked, the standard requires organisations to compare the necessary controls that it has determined with those in ISO/IEC 27001, Annex A. It is important to understand that these Annex A controls are not requirements. The requirement is the cross-checking process.
- The Statement of Applicability (SOA) is required to include all the necessary controls and all excluded Annex A controls. There is no requirement to structure a SOA in terms of Annex A controls. However, it is prudent to be able to show the mapping between necessary controls and Annex A controls.
- Moreover, as explained in ISO/IEC 27003 (“ISMS — Guidance”), necessary controls do not have to be Annex A controls. It refers to necessary controls that are not Annex A controls as custom controls.
- Whilst certification audit plans typically address Annex A controls, the ISO/IEC 27006 (“Requirements for bodies providing audit and certification of ISMS”) requirement is for auditors to review the necessary controls as specified in the organisation’s SOA. If an organisation’s risk treatment plans (RTPs) specify how the necessary controls are intended to modify risk, audit of such RTPs will ensure coverage of the organisation’s necessary controls.
- Fulfilment of the requirements for performance evaluation is best served by first determining the organisation’s information needs, as advocated by ISO/IEC 27004 (“ISMS — Monitoring, measurement, analysis and evaluation”). Thus, first determine what you are going to do with the information that you obtain from monitoring and measuring. It is a good idea to include the fulfilment of your information security objectives in your portfolio of measurements.
- There are just sixteen requirements for documented information, albeit organisations are required to retain documented information on whatever else they deem necessary for the effectiveness of their ISMS.
ISO/IEC 27001:2022/Amd 1:2024 is the third edition (first amendment) of the ISMS standard. The first edition was published in 2005, and the second in 2013.
Changes from the second edition
The most important change is that the content of Annex A has been aligned with the controls in ISO/IEC 27002:2022. However, there are other changes which result from the revised Harmonised Structure.
The Harmonised Structure is part of the ISO Directives that dictate the structure and requirements that are common to all management system standards. It was revised in 2020 to add clarity. However, these changes should not affect existing ISMS that have been properly implemented.
An example
Clause 4.2 has a new bullet point. The clause deals with understanding the needs and expectations of interested parties. The clause already required organisations to determine the interested parties that are relevant to the ISMS and their requirements. The new bullet point requires organisations to determine which of these requirements will be addressed through the ISMS.
An interested party can be a person or entity that can affect an organisation. Thus, as pointed out in ISO/IEC 27005:2022, a hacker is an interested party. Their requirements are for weak security. Notwithstanding that such requirements would be rejected by the organisation and will not become organisational requirements, they will still be addressed through the ISMS — addressed by the information security controls necessary to protect the organisation from such nefarious activities. Organisations should already be doing this.
If a client has a requirement for a service that the organisation chooses not to provide, then provided that requirement it does not become a contractual requirement, it is not relevant to the ISMS (since it does not affect the outcome of the ISMS). In this case, the requirement is not addressed by the ISMS, but then it would never have been.
Thus. the new bullet should have no effect on a properly implemented ISMS.
Other changes are discussed in a BSI publication.
Climate change — the amendment
In common with all other management system standards, ISO/IEC 27001 was amended in February 2024 to clarify that climate change should be consided when determining issues and interested party requirements. Further details can be found here.
Transition arrangements
The three-year transition period has now started – 6 months for accreditation bodies to complete their preparations, 6 months for certification bodies to become accredited for the new standard and then two years for certified organisations to transition to the new standard. However, it is strongly recommended that organisations do not wait — “Since use of the revised Annex A, can discover exposure to unacceptable information security risk, early adoption of ISO/IEC 27001:2022 should be encouraged”.
Further advice
Futher advice on the changes and how to transition your ISMS is given in David Brewer’s new book “An introduction to ISO/IEC 27001:2022/Amd 1:2024”, which is available on Amazon.
Guidance, written by Dr Brewer, is also given on the BSI website, but for a price — £75. His book is cheaper.
There is also a free guide, written by Dr Brewer, to the ISO/IEC 27000 series of standards (numbers 1 to 7) on the BSI website and also to ISO/IEC 27005:2022.
ISO/IEC 27001:2022 is the third edition of the ISMS standard. The principal changes are:
- alignment of Annex A with the controls in ISO/IEC 27002:2022
- alignment with the revised Harmonised Structure (HS) for management system standards
- an amendment, common to all management system standards, for climate change.

David Brewer’s book “An introduction to ISO/IEC 27001:2022/Amd 1:2024”, gives a detailed explanation of the whole of ISO/IEC 27001:2022/Amd 1:2024 including these new requirements. It is available on Amazon in e-book (£36.00) and paperback formats (price £42.25).
Whilst there was very little change to the Information security requirements, one of the most challenging and perplexing aspects of ISO/IEC 27001, is still risk assessment and the SOA, but that can easily be mastered, as can measuring performance, optimising, showcasing and exploiting your ISMS.
The devil is in the detail
Annex A
In alignment with the controls in ISO/IEC 27002:2022, the new Annex A contains 93 information security controls, presented in four groups: organizational controls, people controls, physical controls, and technological controls; a categorisation referred to as themes. The previous edition contained 114 controls grouped under 14 headings, such as “Information security policies” and “Physical and environmental security”. None of these controls were lost. They were either transferred over to the new edition, not necessarily without modification, or merged. Eleven new controls were added, resulting in a reduced total of 93 controls.
Notwithstanding that 56 controls were carried over from Edition 2, there are subtle differences in the wording of the control text. This means that these controls are not identical to the previous edition. For example, whilst the new 5.1 is formed from merging the old A.5.1.1 and A.5.1.2, the new control text contains the phrase “and acknowledged”, which is entirely new.
The new Annex A controls refer to personnel, rather than employees, in recognition of the fact that an organisation need not be a legal entity, in which case the members of the organisation are not employees.
The notes in ISO/IEC 27001, Clause 6.1.3 c) that refer to Annex A were modified to accord with the revised content and to stress that the Annex A controls are not requirements.
Harmonised structure (HS)
All management system standards must conform to the ISO directives. One of these, known as Annex SL presents the structure and requirements that are common to all management system standards. It was revised in 2020. Thus, the revised ISO/IEC 27001 conforms to this new structure,
The principal changes were:
- References to the ISO and IEC online terminology databases were added to Clause 2, albeit that readers are still referred to ISO/IEC 27000 as the source for all terms and definitions.
- A new clause was added to Clause 4.2 (Understanding the needs and expectations of interested parties) which requires organisations to determine which interested party requirements will be addressed through the ISMS.
- Clause 4.4 (Information security management system) now includes the phrase “including the processes needed and their interaction”.
- A note explaining the meaning of the term “business” has been added to Clause 5.1, although the term is still omitted in the reference to “processes” in Clause 5.1 b) (the HS says “…integrated into…business processes”).
- Clause 5.3 now includes the phrase “within the organisation”. The phrase refers to the roles, not the extent of the communications.
- Clause 6.2 now includes a requirement to monitor the [fulfilment] of security objectives, thereby providing a link between the requirement 6.2 b) (“…be measurable (if practicable)”) and Clause 9.1 (Measurement, monitoring, analysis and evaluation).
- Clause 6.3 (Planning of changes) is new. It requires organisations to carry out changes to the ISMS in a planned manner.
- The Edition 2 requirements in Clause 7.4 (Communication) to determine “who shall communicate”, and “the communication process” was replaced by “how to communicate”.
- The scope of Clause 8.1 (Operational planning and control) refers to the whole of Clause 6, rather than just 6.1, thus obviating the need for the Edition 2 requirement “The organization…objectives determined in 6.2”, which was removed.
- Also in Clause 8.1, the HS requirements for process criteria were restored. They were not included in Edition 2 as at the time they were considered unnecessary. It was recognised that the ISO/IEC 27001 requirements for “… at planned intervals” provide built-in examples of process criteria and the control of those processes against those criteria. Moreover, organisations will have their own examples, e.g., concerning the on-boarding and off-boarding of personnel.
- The requirement in Clause 8.1 concerning the control of outsourced processes was replaced with the more general requirement for the control of externally provided processes, products and services.
- The paragraph “The organization shall evaluate …” was restored to its original position in the HS, which is at the end of Clause 9.1. In Edition 2, it was positioned at the head of the clause.
- Moreover, the note that was in Clause 9.1 b) (“The methods selected should … to be considered valid”) was merged into the Clause 9.1 b) text.
- In Clause 9.2 (Internal audit) there are some wording changes and subheadings were introduced.
- In Clause 9.3 (Management review), subheadings were introduced and there is a new requirement to consider changes in the needs and expectations of interested parties.
- The order of Clauses 10.1 and 10.2 was reversed, to focus more attention on the objective of improvement.
- The references in the bibliography were updated.
Climate change
An amendment was published on 24 February 2024 concerning climate change. It added a new requirement to Clause 4.1, which is that organisations shall determine whether climate change is a relevant issue, and a note in Clause 4.2 that points out that relevant interested parties can have requirements related to climate change. The amendment is the same for all management system standards.
The amendment is a consequence of the (ISO) London declaration, which aims to foster active consideration of climate science and associated transitions in the development of all new and revised international standards and publications.
For conformance, determine whether climate change has positive and/or a negative effect on the results of your ISMS. For example, does climate change present an unacceptable risk to information security to your ISMS?, can it have a positive effect on information security? Consider also your organisation’s activities that contribute to climate change. Do they contribute to the risks to your ISMS? Are they in keeping with the principles of Environment, Social and Governance (ESG), recently adopted by ISO?
Want to know more?
David Brewer’s book “An introduction to ISO/IEC 27001:2022/Amd 1:2024”, gives a detailed explanation of the whole of ISO/IEC 27001:2022/Amd 1:2024 including these new requirements. It is available on Amazon in e-book and paperback formats.
The book explains:
- the meaning of all the terms used in the standard
- what is an ISMS, its purpose and benefits, the structure of the standard, relationship with other standards and certification
- the core management system requirements (i.e., those that come from the HS) and are therefore common to other management system standards
- the information security specific requirements (risk assessment, risk treatment, the Statement of Applicability…)
and gives:
- implementation advice (including strategies, preparation and project planning, risk assessment methodologies, determining controls in practice…) .
Guidance, written by Dr Brewer, is also given on the BSI website, but for a price — £75. His book is cheaper.
If you have any question about ISO/IEC 27001:2022/Amd 1:2024, just or use the find facility above. We will be pleased to assist.
.jpg)

you consent to that site setting authentication session cookies